New malware variant targets Uyghur Mac users
http://reviews.cnet.com/8301-13727_7-57581397-263/new-malware-variant-targets-uyghur-mac-users/
New malware variant targets Uyghur Mac users
Yet another malware variant is being sent to Uyghur activists via e-mail spam; however, for updated systems the threat is nonexistent.
One of the ongoing malware sagas is a political fight that is targeting Uyghur activist groups in China, where spam e-mail laced with backdoor Trojan horse malware has been continuously delivered to members of these groups in an Advanced Persistent Threat attack.
This week, security company F-secure uncovered yet another variant of this attack being used.
Like prior ones, the new variant takes advantage of old vulnerabilities in Microsoft Word, by sending attachments that will embed the malware in the affected system if the document is opened in an unpatched version of Word.
The malware used has changed a little over the past year, with some versions using Trojans embedded in ZIP files, and others exploiting Word vulnerabilities. F-secure's report shows this latest attempt uses a Word document called "poadasjkdasuodrr.doc," though any document name can likely be used. When opened, the malware contained in it will install two files that attempt to pose as update components to RealPlayer, in the following locations:
~/Library/Application\ Support/.realPlayerUpdate
~/Library/LaunchAgents/realPlayerUpdate.plist
Since these folders are within the user account, the malware used in this attack variant can install itself without user passwords being required. However, another mode of attack does ask for authentication; if it gets it, the malware will then be placed in the global Library folder instead, so it will run for every user on the system.
Using the "launchagent" file, the system will keep the hidden malware in the Application Support folder running, and will attempt connections to a command-and-control server at the URL alma.apple.cloudns.org.
There are easy ways to help detect and delete such malware (though again, these particular attacks target certain groups and the threat to most Mac users is minimal). First, with general safe computing practices you can avoid obvious spam messages, and be sure to only open attachments that are from trusted sources. Additionally, these attacks often exploit known vulnerabilities that have been patched, so always keep your operating system and installed applications up-to-date.
In addition, these attacks use very common and easy-to-detect modes of keeping the malware active on an OS X system, by way of the system launcher folders, which include the various LaunchAgent and LaunchDaemon directories in the system, global, and user libraries. By setting up a monitoring routine that will alert you when a new item is added to these folders, you can keep on top of what programs are attempting to automate or schedule background routines.
Additionally, you can take the extra step and install a reverse firewall such as those offered byObjective Development's Little Snitch and Intego's VirusBarrier suite, to keep tabs on any program that is trying to phone home to remote servers, and block or otherwise manage the attempt.
From F-Secure Blog
http://www.f-secure.com/weblog/archives/00002546.html
| Another Document Targeting Uyghur Mac Users | Posted by Brod @ 13:39 GMT |
We spotted a new variant of the documents used in the cyber attacks against Uyghur back in February.
This variant was first submitted to VirusTotal on April 11 from China. This time it uses IUHRDF, which may be a reference toInternational Uyghur Human Rights & Democracy Foundation, instead of Captain as the author: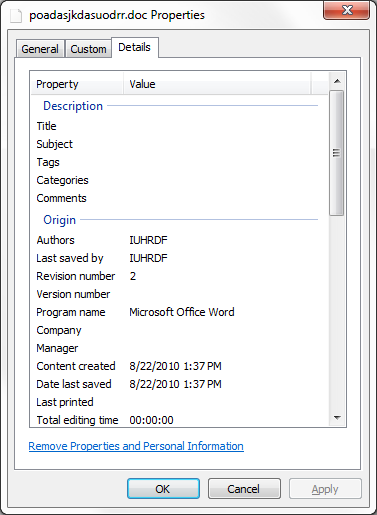
The payload is still the same besides using different filenames and command and control server.
It uses "alma.apple.cloudns.org" as the command and control server: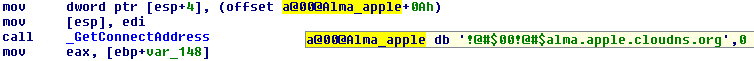
It creates the following copy of itself and launch point:
~/Library/Application Support/.realPlayerUpdate
~/library/launchagents/realPlayerUpdate.plist
Or it may create the following instead (when executed with 2 parameters):
/Library/Application Support/.realPlayerUpdate
/library/LaunchDaemons/realPlayerUpdate.plist
It remains pretty much the same malware and is generically detected as Backdoor SX/CallMe.A since February.
SX/CallMe.A since February.
MD5: ee84c5d626bf8450782f24fd7d2f3ae6 - poadasjkdasuodrr.doc
MD5: 544539ea546e88ff462814ba96afef1a - .realPlayerUpdate
