New Mac Malware Jacksbot
From Intego
http://www.intego.com/mac-security-blog/new-multiplatform-backdoor-jacksbot-discovered/
Excerpt
New Multiplatform Backdoor Jacksbot Discovered
By Lysa Myers on October 12, 2012 • Posted in Malware • View reactions
Update – October 15, 2012
Upon further analysis, it’s been determined that this trojan is the Java RAT created by the hacking and programming group Redpois0n.
____
A new Java backdoor trojan called Java/Jacksbot.A has been discovered that has partial multiplatform support. It is fully functional on Windows, and partially functional on OS X and Linux. This trojan is currently considered low risk as it is not known to have infected users, and it does not run without root permissions. Jacksbot has the usual backdoor functionality, including the following capabilities:
- gathering system information
- taking screenshots
- performing denial of service attacks
- deleting files
- stealing passwords (including specifically Minecraft passwords)
- visiting remote URLs, likely to perform Clickfraud
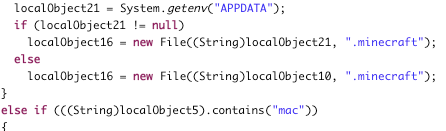 This code is looking for Minecraft passwords.
This code is looking for Minecraft passwords.
It appears likely that this trojan is intended to be dropped by another component that has not yet been identified. The present component will exit with an error message if the Java archive is not run with root permissions. There is also no functionality to trick the user into running the file. We will post additional information about the threat as more is discovered.
Intego VirusBarrier users with up-to-date virus definitions are protected from this threat, which is detected as Java/Jacksbot.A.
Comments
-
Reference URL:- http://news.cnet.com/8301-1009_3-57544407-83/is-new-malware-jacksbot-just-starting-to-rear-its-head/
Is new malware Jacksbot just starting to rear its head?
A new Java-based malware package has been found that has the potential to affect multiple platform.
November 2, 2012 12:26 PM PDTIn the past month a new multiplatform malware package called Jacksbot has been discovered, and while it was initially deemed a minimal threat, it might not stay that way for some Mac, Windows, and Linux users.
Jacksbot is in part a Java-based remote access Trojan (RAT) that appears to be built by a hacking group for the purpose of causing all-too-common malicious activity, including stealing passwords, forcing URLs to load (likely for click fraud), deleting and corrupting files, taking screenshots, logging keystrokes, and otherwise getting personal information.
Java is an attractive platform for criminals to use because being cross-platform means a single coding effort by malware developers can result in a far more distributable attack package that will affect not only different operating systems (Windows, OS X, Linux, etc.) but will also work in multiple Web browsers on these platforms. Security company TrendMicro suggests that the use of Java by the Jacksbot developers means they are in it "for the long haul," so the current findings may be just the tip of something bigger.
When the Trojan was discovered and outlined by Intego earlier in October, it was initially deemed a nonthreat because of its crude nature and seemingly incomplete programming. At the time, the Trojan only partially worked in OS X and Linux, and it seemed to be a component of a larger package such as a downloader or dropper. The Trojan also did not seem to trick users, and it would not run properly without root permissions, which made its coding appear suspicious without being truly "Trojan" in nature.
The Trojan was also not suspected to have infected any PCs; however, following those findings, Trend Micro has found two systems infected with the malware so far. While two systems out of millions of PC systems worldwide is a small number almost pointless to even mention, it does show that the malware is out in the wild, unlike previous suspicions. Whether it takes off and morphs into something more is yet to be seen.
For Mac and Linux systems, the malware is known to add a java execution command to the system's /etc/rc.local and /etc/rc.common files to have it run as an automatically scheduled process at boot. This makes it detectable by checking the contents of the various rc configuration files on the system for any instances of java execution commands. You can do this by opening the Terminal and running the following command:
cat /etc/rc.* | grep java
Since the word "java" should not be included in any of the "rc" configuration files by default, if this command outputs anything before it drops you back to the command line, take a closer look at what the executable is.
For Windows-based systems, you can check the registry for the presence of the following key:
HKEY_CURRENT_USER\Microsoft\Windows\CurrentVersion\Run Microsoft® Windows® Operating System = "{Java Root Directory}\bin\javaw.exe -jar "{Malware Path and File name}""
Again, it must be stressed that so far, this malware has only been seen in two systems, and its coding suggests a focus on executing successfully in Windows rather than other operating systems (though this can easily change). Lastly, it is a Java executable, which requires Java to run; since Java is not an included component of OS X or other operating systems, users with fresh OS installations will not have the infrastructure available for it to run.
As a result, Jacksbot is not known to be much of a threat, but it is still early in its detection; there's always a chance that new variants may surface.
