OSX/KitM.A virus
http://reviews.cnet.com/8301-13727_7-57584804-263/new-mac-spyware-found-in-the-oslo-freedom-forum/
New Mac spyware found in the Oslo Freedom Forum
One surprise is that the new spyware found on Oslo Freedom Forum members' systems has a valid Apple Developer ID.
F-secure is reporting on new malware found for OS X, which appears to be a backdoor application that so far is known to take screenshots of the user's computer and then attempt to upload them to remote servers. The malware is being called OSX/KitM.A.
It's a small application called macs.app and was found on the Mac of an African activist who was a member of of the Oslo Freedom Forum. When installed, the application is appended to the current Mac user's log-in items so it runs whenever the affected user account is logged in. It then takes regular screenshots that it places in a visible folder in the user's home directory called MacApp. It then tries to upload them to the URLs "securitytable.org" and "docsforum.info," which either are not working or are issuing "public access forbidden" error messages.
This bit of malware is somewhat unique in that it is signed with what appears to be a valid Apple Developer ID associated with the name Rajender Kumar. Though not an uncommon name, this may be a reference to the lateBollywood actor of a similar name. Regardless, the use of the ID appears to be an attempt to bypass Apple's Gatekeeper execution prevention technology.
Managing this malware for now involves simply checking one's log-in items (select your username in the Users & Groups system preferences and click the Login Items tab) and removing the macs.app program if present to prevent it from being launched when you log in. Locating and removing the macs.app program file from your computer is also advised; this could be in the Downloads folder, the home directory, or in the Applications folder at the root of the drive.
F-secure is currently investigating the malware to better determine its origin, modes of installation, and how it runs.
http://www.f-secure.com/weblog/archives/00002554.html
| Mac Spyware Found at Oslo Freedom Forum | Posted by Sean @ 12:29 GMT |
The Oslo Freedom Forum is an annual event "exploring how best to challenge authoritarianism and promote free and open societies." This year's conference (which took place May 13-15) had a workshop for freedom of speech activists on how to secure their devices against government monitoring. During the workshop, Jacob Appelbaum actually discovered a new and previously unknown backdoor on an African activist's Mac.
Our Mac analyst (Brod) is currently investigating the sample.
It's signed with an Apple Developer ID.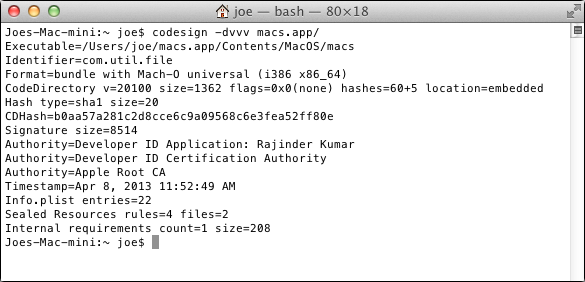
The launch point: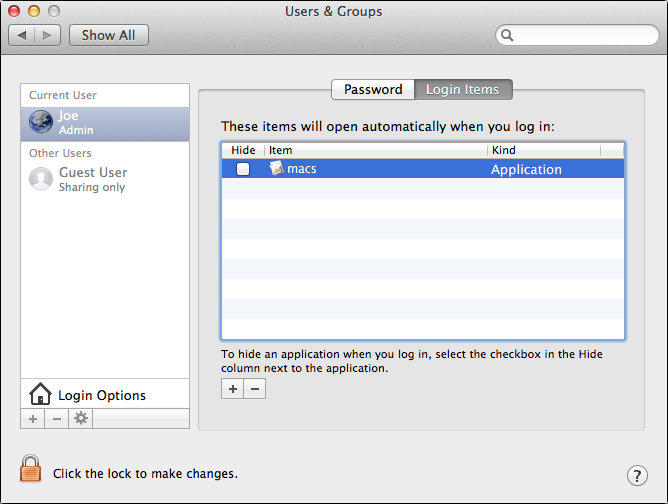
It dumps screenshots into a folder called MacApp: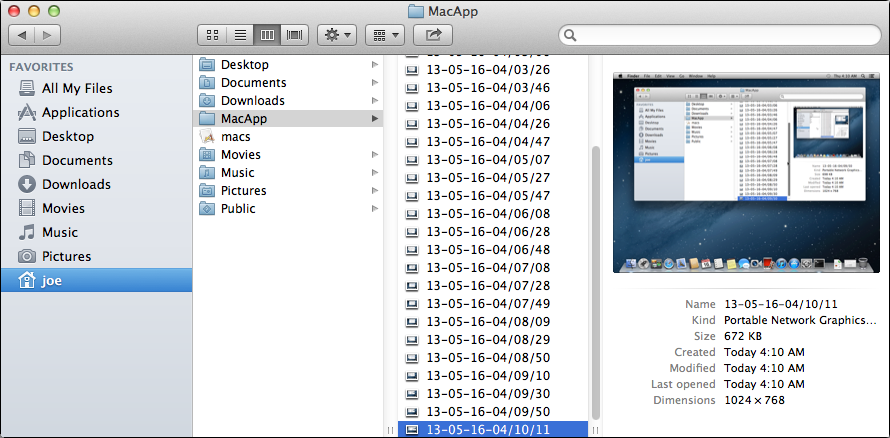
Functions: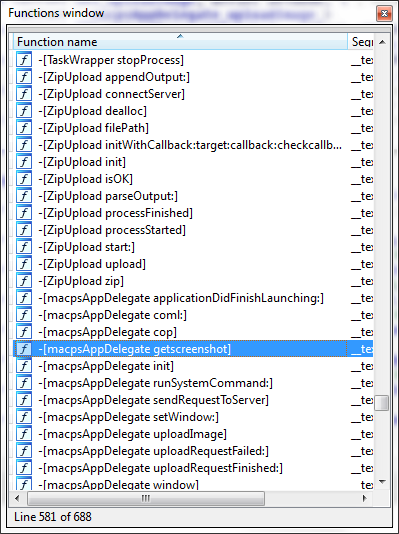
There are two C&C servers related to this sample: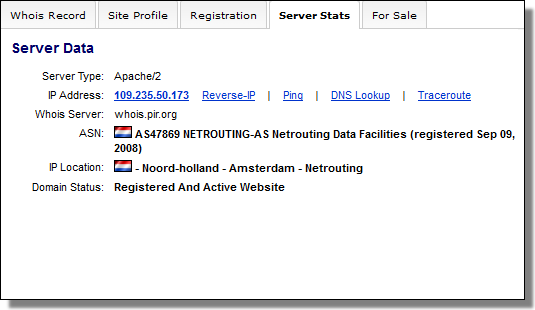
securitytable.org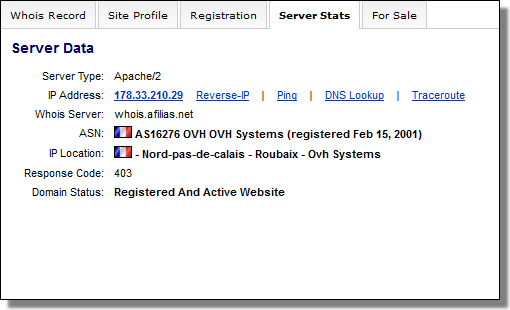
docsforum.info
One C&C doesn't currently resolve, and the other: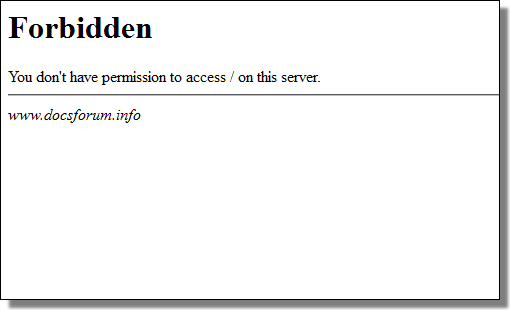
Forbidden
Our detection is called: Backdoor: OSX/KitM.A. (SHA1: 4395a2da164e09721700815ea3f816cddb9d676e)
Comments
-
http://www.f-secure.com/weblog/archives/00002559.html
Mac Spyware Bait: Lebenslauf für Praktitkum Posted by Sean @ 10:12 GMT As a follow up to yesterday's Kumar in the Mac post… have you received e-mail attachments such as this?
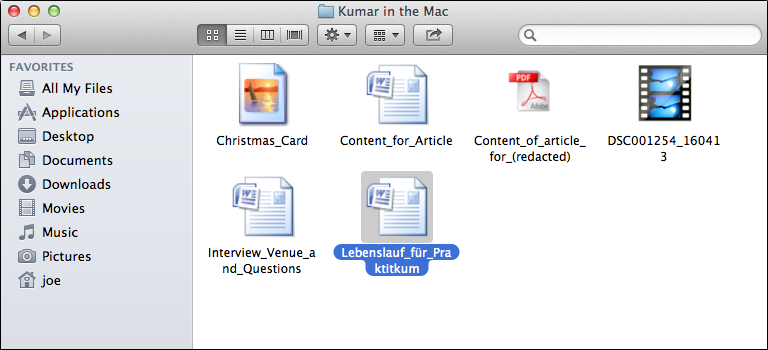
Attachments:
• Christmas_Card.app.zip
• Content_for_Article.app.zip
• Content_of_article_for_[NAME REMOVED].app.zip
• Interview_Venue_and_Questions.zip
• Lebenslauf_für_Praktitkum.zip (Translates as: CV for Internship.)
If so, you may be the target of a spear phishing campaign designed to install a spyware on your Mac.
Here's a list of binaries signed by Apple Developer "Rajinder Kumar".
Detected as Trojan-Spy SX/HackBack.B:
SX/HackBack.B:
• 1eedde872cc14492b2e6570229c0f9bc54b3f258
• 6737d668487000207ce6522ea2b32c7e0bd0b7cb
• a2b8e636eb4930e4bdd3a6c05348da3205b5e8e0
• 505e2e25909710a96739ba16b99201cc60521af9
• 45a4b01ef316fa79c638cb8c28d288996fd9b95a
• 290898b23a85bcd7747589d6f072a844e11eec65 — mentioned in yesterday's post.
Detected as Backdoor SX/KitM.A (includes screenshot feature):
SX/KitM.A (includes screenshot feature):
• 4395a2da164e09721700815ea3f816cddb9d676e
Though the spear phishing payloads are not particularly "sophisticated", the campaign's use of German localization and the target's name (removed in the example above) does indicate the attackers have done some homework.
Be vigilant.
More information:
Mac Spyware Found at Oslo Freedom Forum
Big Hangoverhttp://www.f-secure.com/weblog/archives/00002558.html
Mac Spyware: OSX/KitM (Kumar in the Mac) Posted by Sean @ 12:45 GMT There's another case of Backdoor
 SX/KitM.A in the wild.
SX/KitM.A in the wild.
A German-based investigator reached out to us yesterday regarding OSX/KitM. (We wrote about it last week.) KitM stands for "Kumar in the Mac", which is our designation for spyware — related to OSX/Filesteal a.k.a. OSX/HackBack — that is signed using an Apple Developer ID in the name of Rajinder Kumar. The Developer ID has since been revoked by Apple.
This latest version of OSX/KitM used a Romanian C&C server called liveapple.eu during the period of attack, December 2012 to early February 2013. The spear phishing used an attachment called Christmas_Card.app.zip. (Remember, the attack started in December.)
So, that brings us to this bit of advice for those of you who might be targets.
This is the default "Gatekeeper" security setting: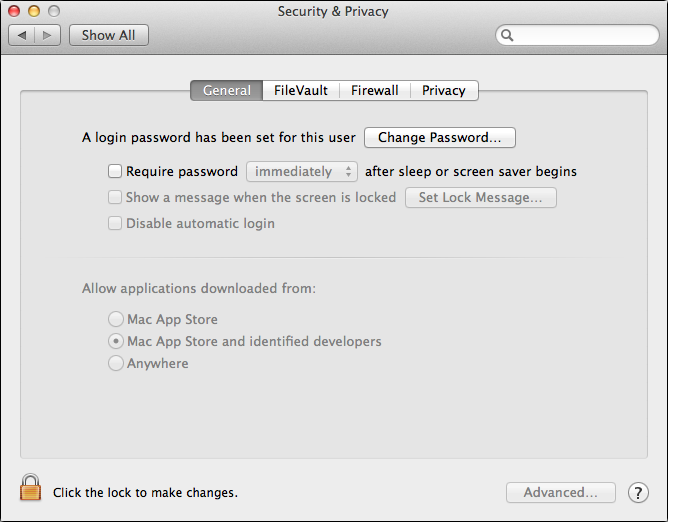
Mac App Store and identified developers
This is the setting that you want, unless you're actively installing software: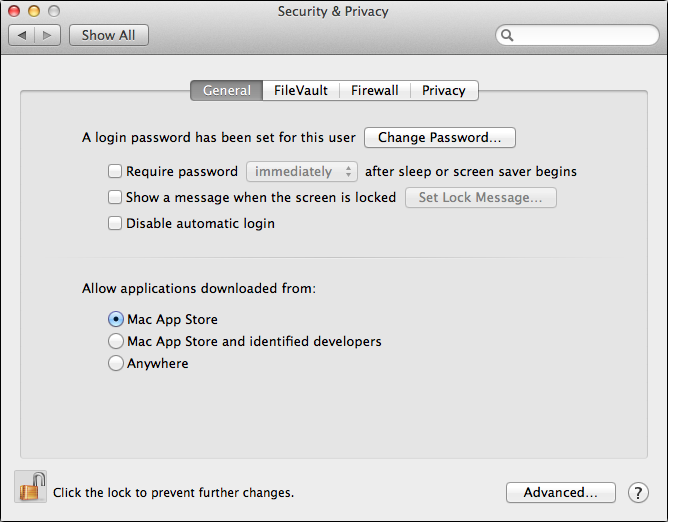
Mac App Store
This is the prompt that results when OSX/KitM attempts to install with the stricter setting: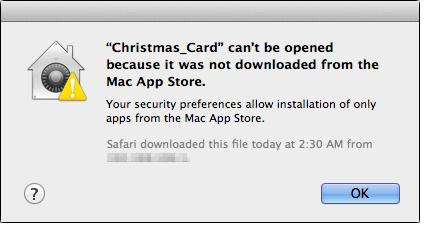
If you're running OS X Mountain Lion or Lion v10.7.5 — adjust your settings as an extra layer of precaution.
SHA1: 290898b23a85bcd7747589d6f072a844e11eec65
