Leaked info - from where?
Answers
-
Hello @Toweri
I can provide basic information, others here may go more in depth. In the past, F-Secure used to show parts of the passwords that were leaked. That was an indicator on which ones I needed to change, besides reviewing them all for password strength. It no longer give us that information, which I find disappointing, as that was one of the features I liked about it.
Your email address has been exposed, but maybe not your client, I would change that password (if possible) using the password generator from within the F-Secure Vault. From within the Vault, I would also check the Password Analysis and review the Weak or Reused passwords and change those, especially and for financial etc. websites. For extra security, I would review all the websites in the Vault, as some of mine had changed how I logged in and wanted me to create a new account which I declined to do, and considered it a dead site (I no longer used, log into). I made sure all had a strong password and used 2FA wherever I could.
From a Perplexity search:
A combolist breach is a data exposure event where your email/username and password appear in a large compiled list that has been built from many different prior data breaches.
What a combolist is
- A combolist is a text file containing many username or email and password pairs (often in
email:passwordformat). - These credentials are usually aggregated from multiple independent breaches, phishing campaigns, and malware “stealer” logs into one large, cleaned list.
What “combolist breach” means for you
- Being in a combolist breach usually means your credentials were not stolen in a brand‑new hack, but were collected from one or more past breaches and bundled into a combo list now circulating among criminals.
- The main risk is credential stuffing: attackers automatically try those username/password pairs on many websites (banks, email, streaming, shopping) hoping you reused the same password.
How serious it is
- Even if the data is “old,” it is still dangerous if you reused that password anywhere or never changed it after the original breach.
- Large public combolists can contain hundreds of millions of unique email and password pairs and are widely traded and reused, so exposure can persist for years.
What to do if you’re in one
- Immediately change passwords for any accounts where you used the exposed password, starting with email, financial accounts, and key services (e.g., cloud storage).
- Enable multi‑factor authentication (MFA) everywhere possible and use unique, randomly generated passwords stored in a password manager to prevent future credential‑stuffing success.
Kind regards.
- A combolist is a text file containing many username or email and password pairs (often in
-
Hello,
Just a little bit of thoughts in addition to the answer above with very sufficient information (and, oh, I'm surprised, since it's a pity that there is no way to see part of the password or the whole one. Which is strange).
I take it, it does not refer to my email service itself…?
Well, I'm not entirely sure, but based on the name of "Combolist" (which could contain completely random stuff other than indicated in its name, and even completely bogus or fake data):
- logsmarket_otc (OTC Logs Market) sounds as a kind of place for obtain stealer logs. This raises the suspicion that the device may have been infected or compromised at some point.
- Privatedata_MARKET may also refer to some 'known' messenger channels, with the same purpose.
Probably in one of the posted (thrown in) portions - your email/password(?) were also included there. Although most likely there could be collected 'logs' from any source (compilations of other combolists with the addition of something "manually" collected), and not exclusively through the collection of data by some group of people.
So, if your email (or an account using that email) was previously leaked, that information could have been included for numbers (so, 'repeated'/'known' one). If not (or it doesn't matter), then it's possible these are logs (or/and credentials, browser cookies, or whatever) from one of your devices or devices where email was typed/used.
In general, infostealer type of malware is quite a thing for mobile devices too (Android-based, for example). So the vector could be anything.
Thus, if the email has not been somehow involved in other incidents (that you know of), then it may be worthwhile, as recommended in the answer above, to check/look at everything that may be connected to this email address and secure it as well.
// If your email address is easy to guess, it's probably just a random registration somewhere by someone who used it on some dubious website (or was simply added to a list). For example, I have a couple of such addresses.. and quite a few "leaks" (even though I have never registered anywhere with this email address).
sorry for spamming.
-
Hi users "TVC15" and "Ukko",
Thank you for your lenghty answers - however they did not answer my question.
As the message I shared indicates, my email and some password associated with that email address have been leaked. One or many times. The password is not shown on the notification message."TVC15", you suggested: "Immediately change passwords for any accounts where you used the exposed password". I ask you, 'Which password?' There is only shown three dots with an underline on that notification as an "exposed password"…
That doesn't really tell me much.The thing is, I have dozens - if not hundreds of logins with my email and a (randomized, mainly 16-character) password.
What I critisize with this notification is, that there is no way for me to know, which of those dozens (or hundreds) of accounts, where I have an account in with my email, are such where I'd need to change my password.
Therefore, this notification is worthless.
As it doesn't reveal - even to me, the owner of those credentials! - what particular password is leaked, it gives me no chance to search that password in my Password Manager to find out, on which web service I need to change the password on.
Or if the password is such that I had already changed on 2018…F-Secure should not send notifications to users, that does not explicitly tell, which password is leaked. It leaves the user with not feasible way to remedy the situation. It just creates anxiety to those who are not sure what they should do - and frustration to us, who would know.
No-one in their right mind would suggest that I changed passwords on each and every account, where I have an account with my email address, would they?
On the other hand, just the pair of my email and a password consisting of completely random characters, with no information where I may have used that particular password, is equally worthless to a potential hacker. They also have no idea, on which service that password is valid for.
To take advantage of it, they would have to blindly try it out on any web service they can think of.
Their chances of finding the right one is overwhelmingly depressing, considering the countermethods any modern web service will have against login flooding. -
Hi @Toweri
"TVC15", you suggested: "Immediately change passwords for any accounts where you used the exposed password". I ask you, 'Which password?' There is only shown three dots with an underline on that notification as an "exposed password"…
That doesn't really tell me much.
When I mentioned change that password, I meant for your email client if possible (your Google Gmail account etc).
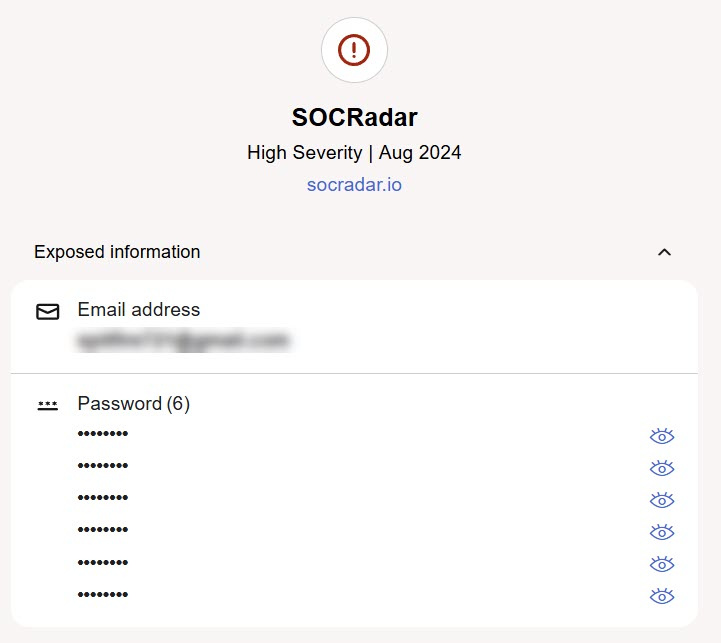
Like I mentioned, they used to give us the parts of the passwords that were compromised, making it easier to know which ones to change. I currently also use McAfee Total Protection with Identity Monitoring (example report below) and it has that option to view (eye icon) parts of the password that were compromised. When I want to review them, McAfee sends a email code for me to unlock the ability to view them/see them (just one time per session, not for every one), and maybe that's why F-Secure quit displaying them, for security reasons in case someone got on our devices and were able to see some of that information?
Since most of your passwords are secure, as you stated, then if you haven't changed the critical ones in a while, maybe do that, and also just go through them in general, not changing everything, just the weak ones, and reused ones?
It can be frustrating with the lack of information, as most of the reports are a combi list type of report (below image), and not so much for individual sites, where hopefully we get a notice from that site if it had been compromised, like Amazon, a mortgage company etc. I've seen this frustration on another AV forum as well regarding their Identity monitoring, but I'm not sure what else can be done in general?
There is the option to Contact support from the blue box in the Identity Monitoring window, and they could maybe explain it better from their end, of what they do and why.
-
Hello,
I just tried with Android 12 phone and beta F-Secure app (I am not sure if it's on up to stable version or a bit behind it). However, I couldn't figure out how to check the email address to see if it contained a recent leak. I mean, no one which I tried was recently related to a breach. All the "old" ones are still displayed with the option to view "all" the leaked data (such as username, password, and so on). Under the "Leaked information" section for chosen confirmed email address. Full and plain password.
Your view is a bit of 'privacy'-related, so to speak. It contains wording like "Other information that got exposed" and password-type is listed under this section. Maybe (as mentioned in other comments above) - now they have stopped showing the password for "fresh" leaks.
For example, it is possible to add any random 'username' and see huge list of breaches/leaks with such 'limited' view of only knowing that 'other information' is also vulnerable now. Because, basically, you cannot confirm 'username' (so, it is not secure to show additional data). And this is the case for old and fresh ones.
Why it is limited in your case - I don't know. Where you tried look at it (mobile, desktop)? Screenshot is about in-app view or is it part of email or something? Which platform?
Anyway,
As the message I shared indicates, my email and some password associated with that email address have been leaked. One or many times. The password is not shown on the notification message.
Just as a random point (and, if not all of 'notifications' are with this limited view): perhaps, password in that particular combolist is not listed in a 'plain text'. So, password is exposed. But listed/provided in hashed-view. So, the pair is something like: "emailAddress:SHA512hash". So, technically - both things are exposed.
But they either failed to provide it or did not provide on purpose there. Like if 'hashed' view is detected and skipped. For example, their system opted to think that it is not relevant to show. But this is if we look for some meaning in this situation and if the password is ever available for display to confirmed email addresses.
For example, looks like that phone number monitoring is only limited to show you that 'data' (and which type) is leaked in relation to monitored phone number. Not really its content.
What I critisize with this notification is, that there is no way for me to know, which of those dozens (or hundreds) of accounts, where I have an account in with my email, are such where I'd need to change my password.
F-Secure should not send notifications to users, that does not explicitly tell, which password is leaked.
Probably. But the point is that this is monitoring of the email address itself and its involvement in leaks. In general, the password may not be affected at all, but only the address or phone number in addition to the email address. Or just the email address. So, F-Secure sends notification to users whenever a monitored item is detected to be 'somewhere' publicly accessible (in malicious/dangerous context).
Why password (or part of it) is not possible to see in your situation - I do not know. But, can you try contact F-Secure via official Support channel and see if they can assist with accessing that information?
On the other hand, just the pair of my email and a password consisting of completely random characters, with no information where I may have used that particular password, is equally worthless to a potential hacker. They also have no idea, on which service that password is valid for.
It is possible that combolists are just a collection of old leaks. If not - they usually(?) come with some context from where stolen credentials are (if they were stolen and not leaked; if they were leaked, then they are part of that known leak).
If to look for some connection in the combolist name in your screenshot, it's possible the "leaked data" was obtained by something like malware. If so, then everything can be considered compromised (where this email was used to log in to a service or website).
If this email was previously known with some leaked password, then most likely it was added to this combo list.
-
Just as additional information:
I received a warning email from F-Secure informing about the leak, prompting me to check the app on my computer.
The leak information (screenshot I provided) is taken from 'fs protection' Beta app UI, "ID Monitoring" section on Windows 11.
The "Password" markings (three dots and an underline) are not clickable links.
Having such markings distinctly dislayed in the warning, yet providing no way to find out, what particular password has been leaked, is in no way heplful. Only worrying (for novices) or frustrating to more advanced users. -
@Toweri I thought I had checked before I had previously posted, but have you checked the information in your F-Secure portal? It does show us the user names that were compromised, just not from within the app itself, maybe for security of our devices, where someone would have to know out portal credentials to see that information?
Again, apologies I didn't catch that previously, as I have multiple PC's with multiple AV's that I compare against each other, which I enjoy doing, and I lost track of that one.
-
-
The "Password" markings (three dots and an underline) are not clickable links.
It just acts as a logo here. To distinguish a section (such as, Exposed information: this, this and this; Where each category with its own 'logo' and 'title').
As shown in @TVC15 latest screenshot, "actual" password(s) are listed under the 'title' with the possibility to unhide them (logo in the right). Where both, "email address" and "password" (and maybe more 'categories'), are placed under "Exposed information".
In your screenshot, for whatever reason 'password' section is listed under "Other information that got exposed". As happened on my phone (Android 12, beta F-Secure app), in this situation, the data itself isn't shown, only the fact of other exposed information in terms of 'category'. For example, if the item being monitored is a phone number or username, then I can't see extra.
But with monitored (confirmed) email address - I can see all stuff (that is provided). However, I really did not find any email address with recent leaks (only old ones). So, I am not sure if 'fresh' ones are just arriving with this limited view.
Since you tried with recently introduced built-in/native design of ID Monitoring in fs protection Windows app (as I think) - maybe - that's the difference now. But I am not sure why.
It looks like my Beta account is not associated with F-Secure portal. I cannot log in with my Beta account.
yes, it should not be possible to do.
you can use beta portal (My FS Protection portal) for beta account. But..
but have you checked the information in your F-Secure portal?
I think this feature is absent in our beta version of the portal (if it is available in My F-Secure in the stable version).
// Even though the changes have been around for quite some time, I still haven't looked at ID Monitoring on the Windows platform. So, I don't know:
- if the password can no longer be viewed there for monitored confirmed email addresses, if it has been "leaked".
- or if this is something specific for your particular case.
-
Hi Ukko,
Thanks, that clarified quite a bit of the oddities I've encountered with this.
Could you please verify, if it should be possible to find the ID Monitoring information on the beta-portal?
Also could you please send me a link to the appropriate beta portal that I can log onto with my Beta account credentials (I am not at all certain, which is beta and which is for the release versions…)
Being able to check the beta portal / ID Monitoring, I can give you definitive description, what do I see there. That might help you pinpoint any account-specific errors (if any.) -
Hello, @Toweri
Sorry for my very late response. I somehow mishandled the fact that you responded.
Could you please verify, if it should be possible to find the ID Monitoring information on the beta-portal?
As I said in my previous comment, I think the beta version of the portal has been doing without this "part" for a long time now.
I think this happened when the 'original' standalone ID Monitoring (F-Secure ID Protection; well.. and I forgot what it was called in the beta) was discontinued and replaced with a built-in design/feature in the F-Secure TOTAL app. The current fs protection beta is the all-in-one solution as well.
So, I am not sure about stable portal (but based on comments by @TVC15 should be the case); but, at least, my beta portal without any extra spaces for either VPN or ID Monitoring or Password Vault things. And just, in general, being a bit more (quite more) outdated in comparison with a stable one.
Also could you please send me a link to the appropriate beta portal that I can log onto with my Beta account credentials (I am not at all certain, which is beta and which is for the release versions…)
In case this ever changes, I'll provide the entire routine.
- https://www.f-secure.com/en/fs-protection (this is current landing page for beta project).
- there is a button named "Access FS Protection" (it will be this URL: https://safeavenue-tp.sp.f-secure.com/iframe/-sso/fs_protection)
- resulted page would be fs protection portal login page; based on your location (? maybe; if there is some relation to regulations or more CDN-based approach; I don't know for sure) and some additional session things. For example, shortened to take less space is resulted page for me via Microsoft Edge (UK/GB). Here I then use my credentials to log in.
So, you can basically (if not sure about password) to use 'Forgot your password?' option.
Being able to check the beta portal / ID Monitoring, I can give you definitive description, what do I see there. That might help you pinpoint any account-specific errors (if any.)
I don't think there should be anything related to ID Monitoring there, but if so - I'd be happy to hear it (and interesting why I don't see it).
Sorry again for late reply. And thanks for your feedback!
// by the way, maybe you could also try as a workaround - create a trial account of the stable F-Secure (with some other email) and see if it will be possible to use ID Monitoring (and if so, then add a "topic" email address for monitoring and see the result)
Because based on Ville's answer in another thread, perhaps the password shouldn't be revealed there either, since the "current" (actual?) backend now(?) only stores password hashes, not the passwords themselves. Meanwhile, information from the old backend might still be accessible for viewing leaked data (then it explains why some passwords of some leaks' content are visible somewhere, which was the experience of me or TVC15 via different routes).
-